Introduction of Cloud Security Architecture
Cloud security architecture is a comprehensive set of policies, technologies, controls, and services that protect data, applications, and related infrastructure for cloud computing. It is designed to provide a secure environment in which you can perform business-critical operations without the risk of data loss or exposure.
Cloud computing-related topics:
- The Ultimate Guide to Cloud Computing: 10 Steps to Implementation Success
- Cloud Computing Reference Models: Explanation and Example with Diagrams
- 7 Big differences between edge computing and cloud computing: Advantages and disadvantages
- Top 9 Cloud Computing Platforms to know in 2024 and Advantages
- 10 Powerful Cloud Computing Applications: All you need to know
Understanding cloud computing security architecture is important for any organization that uses cloud infrastructure or services. It includes elements such as secure data storage, secure network infrastructure, access controls, encryption, and application security measures.
What is cloud security architecture?
A cloud security architecture (sometimes referred to as “cloud computing security architecture”) is defined by the security layers, design, and composition of the platforms, tools, software, infrastructure, and best practices present within a cloud security solution. Cloud security architecture provides a documented, visual model for defining how activities and operations in the cloud are configured and secured. It includes identity and access management, methods and controls for securing applications and data, approaches for achieving and maintaining compliance, threat posture, and overall security visibility; cloud service development; processes for incorporating security principles into operations, policies and governance to meet compliance standards, and physical infrastructure security components.
Cloud security generally refers to the security of information, applications, data, platforms, and infrastructure that operate or reside in the cloud. Cloud security applies to all types of cloud computing infrastructure, including public cloud, private cloud, and hybrid cloud. Cloud security is a type of cybersecurity.
Principles of Cloud Security Architecture
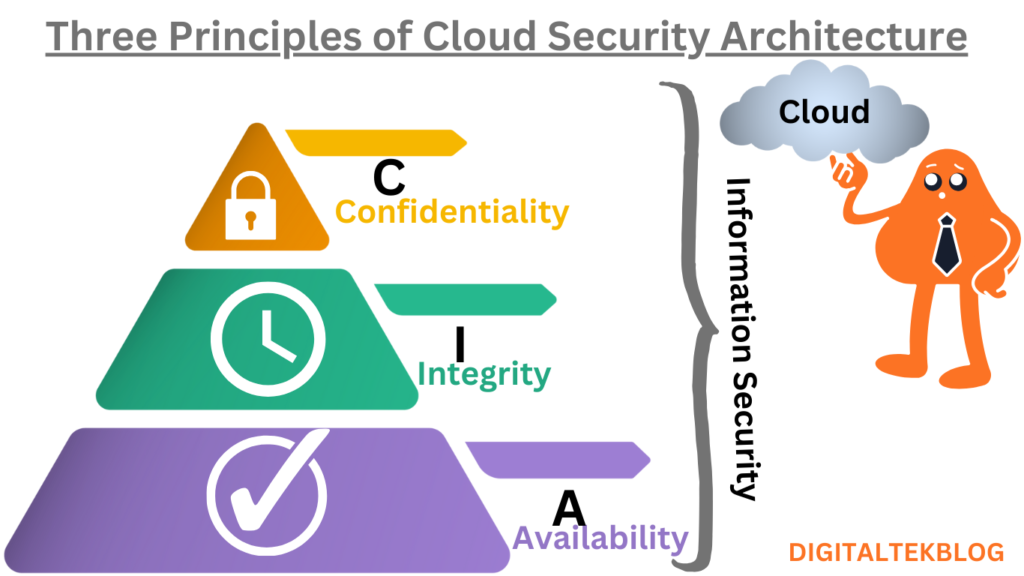
A secure cloud computing architecture includes three core capabilities: confidentiality, integrity, and availability. Understanding each feature can help you plan a more secure cloud deployment.
Cloud security seems complex, but it can be broken down into three main concepts. These are called the “CIA Triad” and are:
- Confidentiality
- Integrity
- Availability
Confidentiality
Confidentiality is the ability to keep information secret so that it cannot be read by anyone who should not have access to it, such as an attacker or someone within an organization who does not have the appropriate level of access. Confidentiality also includes the company’s promise of confidentiality, trust, or secrecy regarding the management of customer data.
Integrity
Integrity is the idea that systems and applications are up-to-date and perform as expected. If a system or application is compromised and produces unknown, unexpected, or misleading output, this can cause harm.
Availability
Availability is the third characteristic and is generally considered the least important by cloud architects. Availability is relevant to denial of service (DoS) attacks. The attacker cannot possibly see or change the data. But if an attacker can make your systems unavailable to you or your customers, you will not be able to perform the tasks necessary to keep your business running.
5 Key Components of Cloud Computing Security Architecture
1. Identity and Access Management (IAM)
Identity and access management (IAM) involves managing who can access cloud resources and what actions they can perform. IAM systems can perform functions such as enforcing security policies, managing user identities, and providing audit trails.
IAM plays a key role in mitigating insider threats. By enforcing minimum privilege access and separation of duties, organizations can limit the potential damage caused by malicious insiders. Additionally, IAM can also help detect abnormal user behavior, providing early warning signs of potential security breaches.
2. Network Security
Network security involves protecting the integrity, confidentiality, and availability of data traveling over a network. Network security measures include firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and virtual private networks (VPN). All cloud providers offer virtual private cloud (VPC) capabilities that allow organizations to run private, secure networks within their cloud data centers.
In cloud environments, network security becomes even more important because data often accesses the cloud via the Internet. Therefore, organizations must prioritize implementing strong network security measures to protect data in transit.
3. Data Security
In cloud computing security architecture, data security involves protecting data at rest, in transit, and in use. It includes a number of measures, such as encryption, tokenization, data loss prevention (DLP), and secure key management. A key aspect of data security in the cloud is enforcing access controls and secure configurations on cloud storage buckets and cloud databases.
With the rise in data breaches and the emergence of regulations such as the General Data Protection Regulation (GDPR), with the added dimension of compliance, data security has become a top priority for organizations. Failing to keep your data secure in the cloud can result in costly fines and legal consequences.
4. Endpoint Security
Endpoint security focuses on securing the endpoints or user devices that access the cloud, such as laptops, smartphones, and tablets. The shift to remote work and bring your own device (BYOD) policies has made endpoint security a critical aspect of cloud computing security. Organizations must ensure that users only access cloud resources using properly secured devices.
Endpoint security measures include antivirus software, firewalls, and device management solutions that can enforce security policies on user devices. Additionally, endpoint security also includes measures such as user training and awareness to help users identify and avoid potential security threats.
5. Application Security
Application security is another important part of cloud security architecture. Protect applications running in the cloud from a variety of security threats, including injection attacks, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Application security can be achieved through a variety of means, including secure coding practices, vulnerability scanning (particularly container image scanning and infrastructure-as-code scanning), and penetration testing. Additionally, runtime application self-protection (RASP) and web application firewalls (WAF) provide additional layers of security.
What is the key reference for the cloud security architecture?
A well-designed cloud security architecture should be based on the following key principles:
- Identity: Knowledge of users, assets, business environments, policies, vulnerabilities and threats that exist within the cloud environment, and risk management strategies (business and supply chain).
- Security controls: Define parameters and policies applicable to users, data, and infrastructure to help manage your overall security posture.
- Security by design: Define control responsibilities, security configurations, and security baseline automation. This is typically standardized and repeatable for deployment across common use cases in accordance with security standards and audit requirements.
- Compliance: Integrate industry standards and regulatory components into your architecture and ensure standards and regulatory responsibilities are met.
- Perimeter security: Protect traffic to and from your organization’s cloud-based resources, including connection points between your company’s cloud network and the public internet.
- Segmentation: Divide the architecture into separate component segments to prevent lateral movement in the event of a breach. This often involves the principle of “least privilege.”
- User Identity and Access Management: Ensure understanding, visibility, and control of all cloud users (people, devices, and systems) accessing corporate assets. Enable access, permissions, and protocol enforcement.
- Data Encryption: Data is encrypted at rest and in transit between internal and external cloud connection points to minimize the impact of a breach.
- Automation: facilitates rapid security and configuration provisioning and updates, as well as rapid threat detection.
- Logging and Monitoring: Captures and continuously monitors (often automated) all activity on connected systems and cloud-based services to ensure compliance, operational visibility, and threat awareness.
- Visibility: This includes tools and processes to maintain visibility across your organization’s multiple cloud deployments.
- Flexible Design: Ensures the architectural design is agile enough to evolve and incorporate new components and solutions without sacrificing underlying security.
What is the importance of cloud computing security architecture?
Cloud technology offers businesses and individual users scalable solutions to meet a variety of user needs. Cloud services offer attractive options for storage, computing power, and application hosting that traditional IT infrastructure cannot provide. Cloud services are extremely flexible and give organizations the storage space they need without requiring upfront investments in additional storage space that may never be used.
While traditional IT infrastructure is often inflexible and requires large capital investments before it can be upgraded, cloud technology provides on-demand access to resources that enable businesses to quickly scale up or down to suit their computing needs and budget. Additionally, with the expertise of cloud security architects like us, who can use cloud security architecture diagrams to identify security gaps and vulnerabilities, organizations can maintain and expand the robustness of their cloud security architecture while maintaining confidence in their cybersecurity stance.
Shared responsibility in cloud security architectures
The type of service model your company uses will determine the type of cloud security architecture that is most appropriate. Cloud security models include Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS).
Organizations that provide cloud services typically follow a shared-responsibility model. In other words, a cloud service provider is responsible for the security of the components (software, compute, storage, databases, networks, hardware, infrastructure, etc.) needed to operate a cloud service. Customers are responsible for the security of data and information stored in the cloud and how that data is accessed (identity and access management). Responsibilities vary slightly depending on the type of service (IaaS, SaaS, or PaaS).
Shared Responsibility for Infrastructure as a Service (IaaS)
With IaaS, a company purchases infrastructure from a cloud provider and typically installs its own operating system, applications, and middleware. An example of IaaS is Azure (Microsoft). With IaaS, customers are typically responsible for the security associated with everything they own or install on their infrastructure.
Shared responsibility for software as a service (SaaS)
With SaaS, an organization purchases use of a cloud-based application from a provider. Examples of SaaS include Office 365 and Salesforce. With SaaS, customers are typically responsible only for security components related to accessing the software, such as identity management and customer network security. The software provider manages the security backend.
Shared responsibility for platform as a service (PaaS)
With PaaS, companies purchase a platform from a cloud provider and develop, run, and manage the application without developing or managing the underlying platform infrastructure needed for the application. An example of PaaS is Amazon Web Services (AWS). With PaaS, the customer is responsible for security related to application implementation, configuration, and permissions.
Cloud Security Architectures by Service Model
IaaS Cloud Security Architecture Components
Components of a secure cloud computing architecture for IaaS cloud environments include endpoint protection (EPP), cloud access security brokers (CASB), vulnerability management solutions, access management, and data and network encryption.
SaaS Cloud Security Architecture Components
SaaS security architecture components should include application security, identity and access management, and a cloud access security broker (CASB). It facilitates visibility, access control, and data protection using APIs, proxies, or gateways.
PaaS Cloud Security Architecture Components
PaaS security architectures may require standard cloud security architecture solutions as well as less common solutions such as cloud workload protection platforms (CWPPs).
Related topics about cloud computing, you should know about:
- Top 8 Examples of IAAS in cloud computing: What You Need To Know In 2024
- Top 5 Advantages of IaaS in cloud computing 2024
- 11 Best Popular Examples Of SaaS in Cloud Computing
- What is SaaS (Software as a Service)? Advantages and disadvantages
- What is Platform as a Service (PaaS)? Advantages and disadvantages
- Infrastructure as a Service (IaaS) in cloud computing: advantage and disadvantages
Top 6 cybersecurity risks
As more businesses move their data and apps to the cloud, the potential for security risks also increases. Cybersecurity risks change over time, but common cloud security risks include:
1. Human error
99% of all cloud security incidents between now and 2025 are expected to be caused by human error. Errors can be small, like using a weak password or accidentally sharing sensitive information. This can lead to larger errors, like incorrect security settings. Organizations can take several steps to reduce the risk of human error. For example, training employees, using automation, and implementing proper change control processes.
2. Denial of service attacks
A DoS attack disrupts a service by sending too many requests. This can cause critical apps, data, and resources to become unavailable in the cloud. DDoS attacks are more sophisticated than DoS attacks and can be very destructive. Organizations should use cloud-based DDoS protection to protect against these attacks. You can also install firewalls and intrusion prevention systems to protect your cloud resources.
3. Hardware strength
The strength of the physical hardware used for cloud services is of the utmost importance. Enterprises should carefully consider the hardware offerings of their cloud service providers (CSPs). Users can also use a special device called a hardware security module (HSM). These are used to protect encryption codes and ensure data security.
4. Insider attack
Insider attacks can be carried out by current or former employees or key service providers. These are extremely costly, costing businesses an average of $15.38 million in 2021. To thwart these attacks, organizations must have strict access control policies. This includes regularly checking access and monitoring unusual user behavior. Additionally, users should only be given access to what they need to do their job.
5. Shadow IT
Shadow IT occurs when users use apps, devices, or services that they are not authorized to use. Easy-to-use cloud services are an obvious culprit for shadow IT. This can lead to data breaches, compliance issues, and security issues. Organizations must have clear rules regarding the use of cloud services. All policies to handle this should be run through centralized IT control.
6. Cloud Edge
Data is considered to be at the cloud edge if it is processed close to the data center rather than in the data center. The problem is that the edge of the cloud is vulnerable to attack. There are more places to attack and sensitive data may be stored in less secure locations. Enterprises must ensure that security policies are applied to edge devices and networks. All data should be encrypted and use the latest application security patches.
Six steps to secure your cloud
Now that you know the biggest security risks, you can consider how to protect your cloud architecture from those risks.
An important aspect of cloud security practices is managing access to cloud resources. Deciding who has access and what they can do can make a significant difference in security. The identity and access management (IAM) security model helps with this. Companies can achieve this by controlling user access based on roles and responsibilities. IAM security requirements include:
1. Authentication
Authentication confirms users’ identities when they access data. On the surface, this means asking for a username and password. More advanced methods include multi-factor authentication for apps and user segmentation. Multi-factor authentication requires users to provide two or more forms of evidence.
2. Approval
Authorization is the process of granting access to resources based on a user’s role and permissions. It ensures that users only access the data and services they need to do their job. Restricting access reduces the risk of unauthorized users. Role-based access control (RBAC) is one way to do this in a cloud environment. It grants users access based on their job function.
3. Auditing
Auditing involves monitoring and recording user activity in your cloud environment. This allows you to detect potential security issues and maintain access logs. By regularly reviewing access logs, organizations can identify unusual patterns or suspicious behavior.
4. Encryption at rest and in transit
Data at rest is data that is not in use, and data in transit is data that is sent between devices or users. Encryption is a way to protect data from unauthorized access. This is done by converting it into a code that only someone with the right key can read. When storing data in the cloud, it is important to encrypt it to protect it from prying eyes. Many cloud service providers have built-in encryption for data at rest.
For data in transit, encryption methods such as SSL/TLS help prevent eavesdropping. This ensures security when sensitive information moves between networks.
5. Network Security and Firewalls
Good network security controls are essential to keeping your cloud environment secure. Using a firewall to control traffic is a critical network security measure. A firewall is a gatekeeper, blocking certain types of connections based on rules.
Intrusion Detection and Prevention Systems (IDPS) are also important network security tools. IDPS tools monitor network traffic for signs of unauthorized activity, such as hacking or malware. It can then automatically block or alert administrators about potential threats. This allows organizations to quickly respond to security incidents and minimize damage.
6. Version Control and Logging
Versioning is the practice of keeping track of different versions of cloud resources, such as apps and data. This allows businesses to revert to previous versions in the event of a security incident or data breach. Maintaining version history allows organizations to identify and remediate security vulnerabilities.
follow me : Twitter, Facebook, LinkedIn, and Instagram


2 thoughts on “Best 5 Key Components of Cloud Security Architecture”
Comments are closed.