What is a digital signature?
We have long used handwritten signatures to authenticate handwritten or typed messages in the physical world. Their primary use is to link signers to specific messages. A digital signature functions similarly to a digital message. The signer, i.e., the person or entity, is tied to the digital data. This binding can be verified by the recipient or a third party, if desired.
In cryptography, a digital signature is a value calculated from data with a private key that is known only to the signer. The recipient must vouch that the message is from the sender. This is very important in business, as there is a possibility of disputes arising over data exchange.
Algorithms of digital signature in cryptography
There are three algorithms at work in digital signatures. They are as follows:
1. Key generation algorithm
Key generation algorithms help ensure authenticity and integrity. Otherwise, it becomes very easy to tamper with the data. It also prevents people from impersonating the sender.
2. Signature algorithm
A signature algorithm creates a one-way hash of the data that needs to be signed. Then encrypt the hash value using the signing key. The encrypted hash and other information are a digital signature.
3. Signature verification algorithm
Signature verification algorithms help process digital signatures and verification keys to generate value. This algorithm also processes the same hash function on the received data to create a hash value.
Digital signature in cryptography model
As mentioned earlier, digital signature schemes are based on public-key cryptography. The model of the digital signature scheme is shown in the following figure:
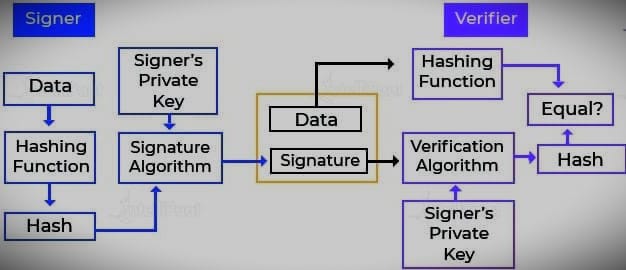
The following points explain the entire process in detail:
- Each person using this method has a public and private key pair.
- Typically, the key pairs used for encryption/decryption and signing/verification are different. The private key used for signing is called the signing key, and the public key is called the verification key.
- The signer feeds the data into a hash function to generate a hash of the data.
- The hash value and signature key are fed into a signature algorithm, which generates a digital signature on the specified hash. A signature is added to the data, and both are sent to the verifier.
- The verifier inputs the digital signature and verification key into the verification algorithm. Verification algorithms give some value as output.
- The verifier also performs the same hash function on the received data to generate the hash value.
Verification compares this hash value with the output of the verification algorithm. Based on the comparison results, the verifier determines whether the digital signature is valid or not.
- A digital signature is created by the signer’s “private” key, which no one else can have. Signers cannot refuse to sign data in the future.
Note that instead of signing the data directly, the signature algorithm typically creates a hash of the data. Since the hash of the data is a unique representation of the data, it is sufficient to sign the hash instead of the data. The most important reason for using hashes instead of direct data for signatures is the efficiency of the scheme.
Assume that RSA is used as the signature algorithm. As explained in the Public Key Cryptography chapter, the encryption and signing process using RSA involves a modular exponentiation operation.
Signing big data using modular exponentiation operations is computationally expensive and time-consuming. Because the hash of the data is a relatively small digest of the data, signing the hash is more efficient than signing the entire data.
Know more about cybersecurity and cryptography:
- Cryptography and network security
- Cryptography: Meaning, Types and best Example—everything is here to know
- What is malware? History, Definition, 7 main types and real-world examples
- 3 Main Objectives of Cybersecurity
- Cybersecurity Goals: 3 major objectives of cybersecurity
- The top 7 cybersecurity courses online for beginners 2024
Importance of Digital Signature
Among all cryptographic primitives, digital signatures using public-key cryptography are considered a very important and useful tool for achieving information security.
In addition to the ability to provide message non-repudiation capability, digital signatures also provide message authentication and data integrity. Let’s take a look at how this is achieved through digital signatures:
- Message authentication: When a verifier uses the sender’s public key to verify a digital signature, it ensures that the signature was created only by the sender and not by anyone else who has the corresponding secret private key.
- Data integrity: If an attacker accesses the data and modifies it, the digital signature verification fails at the recipient end. The hashing of the modified data and the output provided by the verification algorithm do not match. Therefore, the recipient can safely reject the message, assuming that data integrity has been compromised.
- Non-repudiation: It is assumed that only the signer knows the signing key, so the signer can only create a unique signature on specific data. Therefore, the recipient can present the data and digital signature to third parties as evidence in case of any future disputes.
By adding public-key cryptography to a digital signature scheme, you can create a cryptographic system that can provide the four essential elements of security: confidentiality, authentication, integrity, and non-repudiation.
Encryption with Digital Signature
In many digital communications, it is desirable to exchange encrypted messages rather than plain text to ensure confidentiality. In public-key cryptography, the sender’s public (encryption) key is available in the open domain, allowing anyone to hide their identity and send an encrypted message to a recipient.
This makes it necessary for users who use PKC for encryption to require digital signatures along with the encrypted data to ensure message authentication and non-repudiation.
It may be stored using a combination of digital signatures and encryption schemes. Let us briefly discuss how to achieve this requirement. There are two possibilities: sign then encrypt or encrypt then sign.
However, cryptographic systems based on signing and then encrypting can be misused by the recipient to hide the identity of the sender and send that data to a third party. Therefore, this method is not preferred. The encrypt-then-sign process is more reliable and widely adopted. This is shown in the following figure –
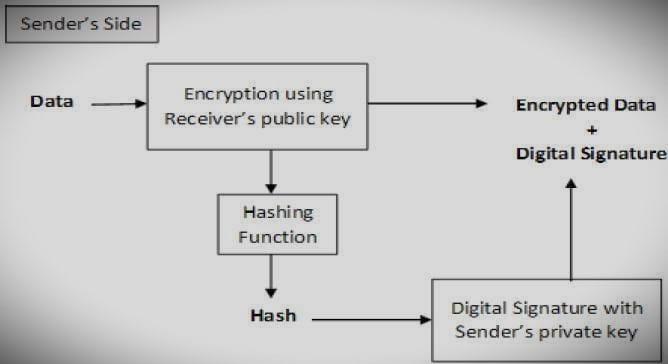
After receiving the encrypted data and its signature, the recipient first verifies the signature using the sender’s public key. After verifying the validity of the signature, use your private key to decrypt it and recover the data.
How do I create a digital signature?
A digital signature is based on public key cryptography. Let’s look at how a digital signature is created:

- A person who employs a digital signature scheme has a public and private key pair.
- Encrypt/decrypt and sign/verify pairs are usually different. The signing key is the private key used for signing, and the verification key is the public key.
- The signer feeds all the data into the hash function and generates a hash of the data.
- The signature key and hash value are input to the signature algorithm, which generates a digital signature based on the specified hash. Once the signature is added to the data, both are sent to the verifier.
The verifier then inputs the digital signature and verification key into the verification algorithm. The validation algorithm produces an output value.
- The verifier is also responsible for performing some hashing functions on the received data to generate a hash value.
Verification is handled by comparing the hash value generated by the verifier with the output of the verification algorithm. The results of this comparison help verifiers determine whether the digital signature is valid or not.
- No one else has access to the signer’s private key, and the digital signature is created using this key, so the signer cannot deny signing documents in the future.
follow me : Twitter, Facebook, LinkedIn, Instagram
