What is a phishing attack?
A phishing attacks is a type of social engineering attack commonly used to steal user data, such as login credentials and credit card numbers. This occurs when an attacker pretends to be a trusted entity and tricks the victim into opening an email, instant message, or text message. Recipients may be tricked into clicking malicious links, leading to malware installation, system freeze as part of a ransomware attack, or sensitive information being leaked.
Since the mid-1990s, the term “phishing” has been used to identify hackers who use fraudulent emails to “extort” information from unsuspecting users. However, phishing attacks have become increasingly sophisticated and are now classified into different types, including email phishing, spear phishing, smishing, vishing, and whaling. Each type is characterized by specific channels and execution methods, such as email, text, voice, and social media, and all have similar underlying intentions.
Phishing attacks can have devastating consequences. For individuals, this includes fraudulent purchases, theft of funds, or identity theft.
Additionally, phishing is often used as part of larger attacks, such as advanced persistent threat (APT) incidents, to gain a foothold in corporate and government networks. In the latter scenario, employees have to compromise to circumvent security limitations, distribute malware in closed environments, or gain privileged access to protected data.
Organizations that become victims of such attacks typically suffer severe financial losses in addition to loss of market share, reputation, and consumer trust. Depending on the scope, a phishing attempt could turn into a security incident, making it difficult for your company to recover from.
Working technology of Phishing attack
Whether a phishing campaign is targeted or sent to as many victims as possible, it starts with a malicious message. The phishing attacks masquerade as a message from a legitimate company. The more aspects of the message mimic a real company, the more likely an attacker will be successful.
The goals of attackers vary, but a common goal is to steal personal information or credentials. Emphasizing the urgency of the message facilitates the attack, which can lead to account suspension, loss of funds, or the targeted user’s job loss. A user fooled by an attacker’s request does not have time to stop and consider whether the request is reasonable or the source is legitimate.
As phishing attacks continue to evolve to evade security filters and human detection, organizations must continually train their employees to stay abreast of the latest phishing tactics. It only takes one phishing attempt to cause a major data breach. Thus, it is one of the most important threats to mitigate and the most difficult because it requires human protection.
Why is phishing a problem?
Phishing is a serious problem because it is easy, cheap, and effective for cyber criminals to use. Phishing tactics, especially emails, require minimal cost and effort, making them a widespread cyber attack. Victims of phishing scams may suffer malware infections (including ransomware), identity theft, and data loss.
Cybercriminals target personally identifiable information (PII) such as financial account data, credit card numbers, tax and medical records, as well as sensitive data such as customer names and contact information, proprietary product secrets and confidential information. This includes business data. Communications.
Cybercriminals also use phishing attacks to gain direct access to email, social media, and other accounts, as well as allow connected systems such as point-of-sale terminals and order processing systems to be modified or compromised. . Many large-scale data breaches begin with a harmless phishing email, allowing cybercriminals to gain a small.
Example of Phishing Attacks
Attackers often use strategies to exploit the feeling of fear and distress, telling users that their accounts will be restricted or suspended if they do not respond to emails.
Phishing attacks are usually sent to as many people as possible, so the messages are usually thin and generic. Below are some examples of common phishing emails.
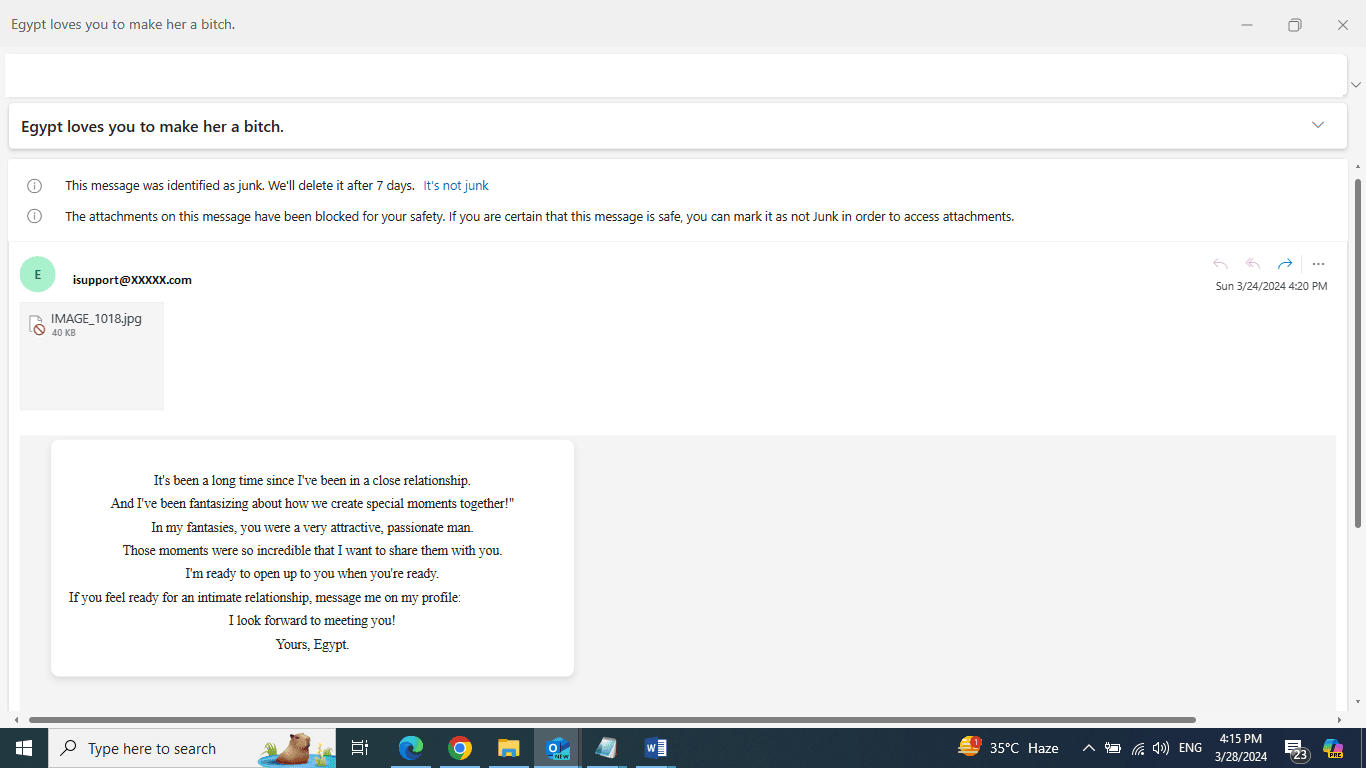
The user’s name is not mentioned in the above message, and the sense of urgency is used to create fear and trick the user into opening the attachment.
Attachments may be web pages, shell scripts (such as PowerShell), or Microsoft Office documents that contain malicious macros. These macros and scripts can be used to download malware or trick users into revealing their account credentials.
Some email phishing tactics involve attackers registering domains that resemble official domains or, in some cases, using common email providers such as Gmail. When a user receives an email, the message may use the company’s official logo, but the sender’s address does not include the company’s official domain. How an attacker executes a phishing campaign depends on their target. For example, in B2B, an attacker can use a fake invoice to trick the accounts payable department into transferring money. In this attack, the sender is not as important as the message. Many sellers use personal email accounts to conduct business.
Phishing Techniques
Cybercriminals use three primary phishing techniques to steal information:
- Malicious web links
- Malicious attachments and
- Fraudulent data-entry forms.
Malicious Web Links
Phishing leads users to fake websites or sites infected with malicious software, also known as malware. Malicious links can be disguised as trustworthy links and embedded in logos or other images within the email.
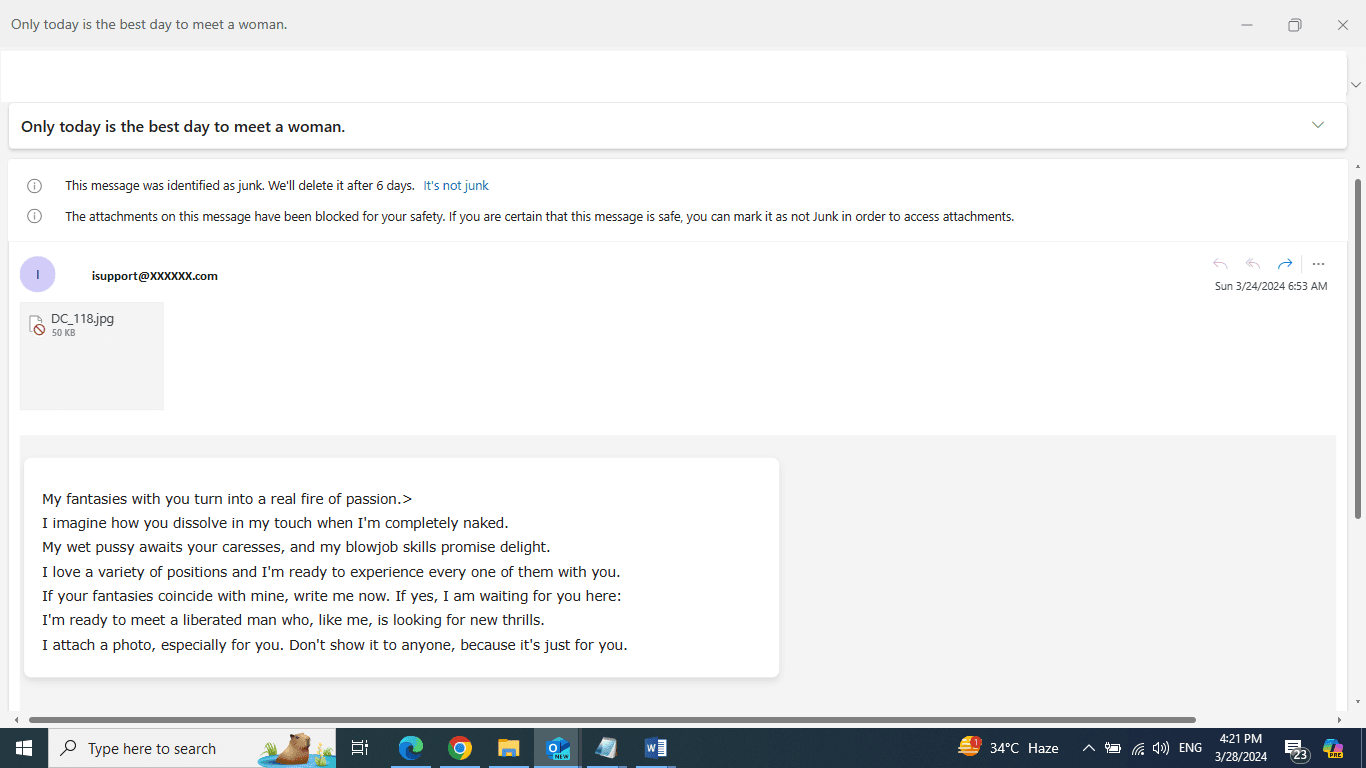
Malicious Attachments
While these may seem to be real record connections, they are really contaminated with malware that you can think twice about and their documents.
Fraudulent Data Entry Forms
These techniques use fake forms that ask users to enter sensitive information such as user ID, password, credit card data, and phone number. Once users submit that information, cybercriminals can use it to conduct various fraudulent activities, including identity theft.
Related Topics about cybersecurity that you should know
- What is malware? History, Definition, 7 main types and real-world examples
- 3 Main Objectives of Cybersecurity
- Cybersecurity Goals: 3 major objectives of cybersecurity
- Cryptography digital signature: Definitions, Algorithms and importance
- Cryptography and network security
- Cryptography: Meaning, Types and best Example—everything is here to know
- The top 7 cybersecurity courses online for beginners 2024
Types of Phishing Attacks
Phishing has evolved into much more than just credential and data theft. The way attackers run their campaigns depends on the type of phishing.
Types of phishing include:
- Email phishing is a general term for malicious email messages designed to trick users into revealing personal information. Attackers’ goals are typically to steal account credentials, personally identifiable information (PII), and trade secrets. However, attackers targeting specific businesses may have other motivations.
- Spear phishing: These email messages are sent to specific people within an organization (usually high-privileged account holders) in an attempt to leak sensitive data, send money to an attacker, or download malware.
- Link manipulation: The message contains a link to a malicious site that looks like an official business, but the recipient is directed to a server controlled by the attacker, where they send their credentials to the attacker. You will be directed to the fake login page to authenticate.
- Whaling (CEO fraud): These messages are typically sent to key employees of a company to trick them into believing that the CEO or other executive has requested a money transfer. CEO scams are classified as phishing, but instead of impersonating a popular website, the attacker impersonates the CEO of the target company.
- Content injection: Attackers who inject malicious content into official sites can trick users into visiting the site, display malicious pop-ups, or redirect them to phishing websites.
- Malware: Users who are tricked into clicking a link or opening an attachment may download malware to their device. Ransomware, rootkits, or keyloggers are common malware attachments that steal data and extort payment from targeted victims.
- Smishing: Attackers use SMS messages to trick users into visiting malicious sites from their smartphones. Attackers send targeted victims text messages containing malicious links that promise discounts, offers, or free rewards.
- Vishing: Attackers use voice-altering software to leave a message to the targeted victim telling them they should call a potentially fraudulent number. Voice changers are also used when speaking to targeted victims to disguise the accent and gender of the attacker and to impersonate the scammer.
- “Evil Twin” Wi-Fi: By spoofing free Wi-Fi, attackers can trick users into connecting to malicious hotspots and carry out man-in-the-middle attacks.
- Pharming: Pharming is a two-step attack that is used to steal account credentials. The first step involves installing malware on the targeted victim and redirecting them to their browser or a fake website, where they are tricked into revealing their credentials. DNS poisoning is also used to redirect users to fake domains.
- Angler phishing: Attackers use social media to respond to posts pretending to be from official organizations, tricking users into revealing account credentials and personal information.
- Watering Holes: Compromised sites provide attackers with endless opportunities to identify sites used by large numbers of targeted users, exploit site vulnerabilities, and trick users into downloading malware. Use the. Once the malware is installed on the target user’s machine, the attacker can redirect the user to a fake website or deliver a payload over the local network to steal data.
Frequently Asked Questions (FAQs)
What are the 4 types of phishing?
- Spear Phishing.
- Whaling.
- Vishing.
- Email Phishing.
What are the 4 ways to avoid phishing?
- Protect your computer by using security software.
- Protect your cell phone by setting the software to update automatically.
- Protect your accounts by using multi-factor authentication.
- Protect your data by backing it up.
follow me : Twitter, Facebook, LinkedIn, Instagram


1 thought on “Phishing Attacks Explained – What They Are & How to Prevent Them”
Comments are closed.