Definition of Network Security
Network security includes all steps taken to protect the integrity of a computer network and the data within that network. Network security is important because it protects sensitive data from cyberattacks and ensures that networks are available and reliable. A successful network security strategy uses multiple security solutions to protect users and organizations from cyber attacks such as malware and distributed denial of service.
A network consists of interconnected devices such as computers, servers, and wireless networks. Many of these devices are vulnerable to potential attackers. Network security involves the use of various software and hardware tools on your network or as software-as-a-service. As networks become more complex and enterprises rely on them and data to conduct business, security becomes more important. As threat actors create new attack vectors on these increasingly complex networks, security technologies must also evolve.
Security is typically framed as everyone’s responsibility, as every user on the network presents potential vulnerabilities within the network, regardless of specific methodology or corporate security strategy.
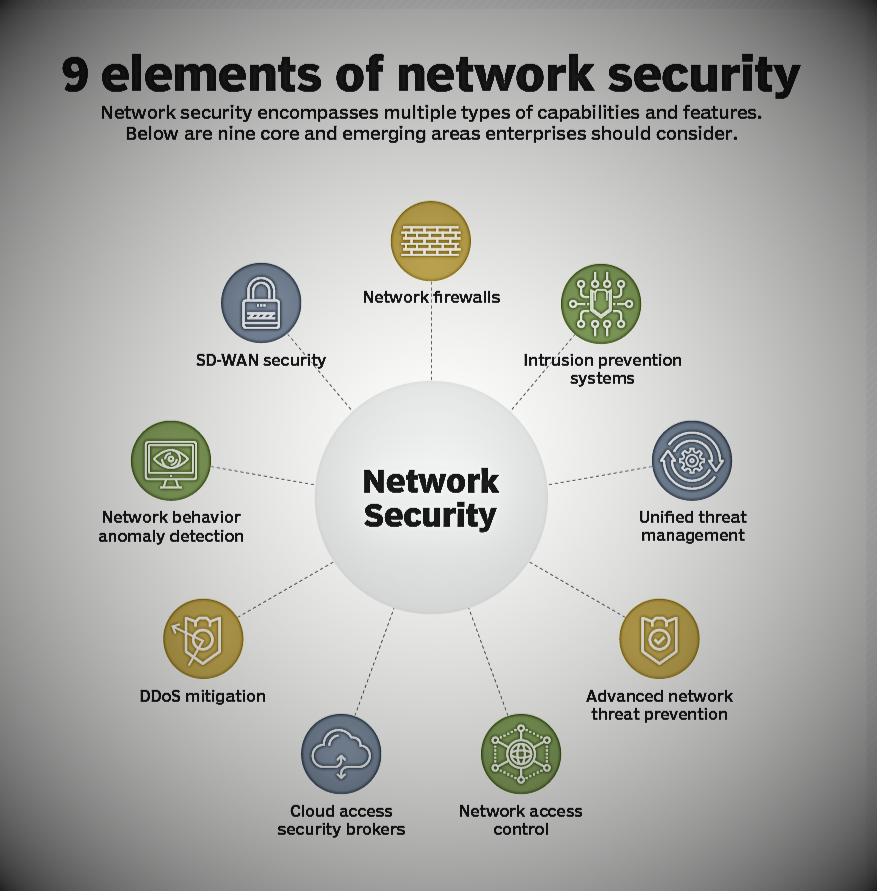
How does network security work?
Network security is enhanced using a combination of hardware and software tools. The primary purpose of network security is to prevent unauthorized access between a network or parts of a network.
A security officer or team sets strategies and policies that help keep an organization’s network secure and compliant with security standards and regulations. Everyone on your network must follow these security policies. Every point in the network where data can be accessed by an authorized user is also a point where data can be compromised by a malicious attacker or through user inattention or mistake.
Types of network security software and tools
- Security policies and device options vary from network to network and change over time. Strong security often uses multiple approaches, known as layered security or defense in depth, to provide organizations with as much security control as possible. The following are types of commonly used network security tools and software.
- Access control. This method limits access to network applications and systems to specific groups of users and devices. These systems deny access to users and devices that are not yet authorized.
- Antivirus and antimalware. Antivirus and antimalware are software designed to detect, remove, or prevent viruses and malware such as Trojan horses, ransomware, and spyware from infecting your computer and, by extension, your network.
- Application security. It is extremely important for organizations to monitor and secure the applications they use to run their business. This is true whether your organization builds or buys the application. Modern malware threats often target open source code and containers that organizations use to build software and applications.
- Behavioral analysis. This method analyzes network behavior and automatically detects and alerts organizations about unusual activity.
- Cloud Protection. Cloud providers often sell add-on cloud security tools that add security features to the cloud. Cloud providers provide tools to users to manage security across their infrastructure and protect instances within the entire cloud infrastructure. For example, Amazon Web Services provides security groups to control inbound and outbound traffic associated with an application or resource.
- Data Loss Prevention (DLP). These tools monitor data in use, in motion, and at rest to detect and prevent data breaches. DLP often categorizes the data that is most important and at risk and trains employees on best practices for protecting that data. For example, not sending important files as email attachments is one of such best practices.
- Email security. Email is one of the weakest points in your network. Employees become victims of phishing and malware attacks when they click on links in emails that secretly download malicious software. Email is also an unsafe way for employees to unknowingly send files and sensitive data.
- Firewall. Software or firmware inspects incoming and outgoing traffic to prevent unauthorized network access. Firewall is one of the most widely used security tools. These are placed in several areas on the network. Next-generation firewalls increase protection against application-layer attacks and provide advanced malware protection with inline deep packet inspection.
- Intrusion Detection System (IDS). IDS detects unauthorized access attempts and flags them as potentially dangerous, but does not remove them. IDSs and intrusion prevention systems (IPS) are often used in conjunction with firewalls.
- Unauthorized entry prevention system. IPS is designed to prevent intrusions by detecting and blocking attempts to gain unauthorized access to your network.
- Mobile device security. Business applications on smartphones and other mobile devices have made these devices an important part of network security. Monitoring and controlling which mobile devices access the network and their behavior once connected to the network is critical to modern network security.
- Multi-factor authentication (MFA). MFA is an easy-to-implement and increasingly popular network security solution that requires two or more factors to verify a user’s identity. An example of this is Google Authenticator, an app that generates a unique security code that users enter along with their password to verify their identity.
- Network segmentation. Organizations with large networks and network traffic often use network segmentation to divide their networks into smaller, more manageable segments. This approach gives organizations greater control and visibility over traffic flow. Industrial network security is a subset of network segmentation that increases visibility into industrial control systems (ICS). ICS is increasingly integrated with the cloud, increasing its exposure to cyber threats.
- Sandboxing. This approach allows organizations to open files in an isolated environment and scan for malware before allowing access to the network. Opening in a sandbox allows organizations to see if a file behaves maliciously or shows signs of malware.
- Security Information and Event Management (SIEM). This security management technology logs data from applications and network hardware and monitors suspicious behavior. When an anomaly is detected, the SIEM system alerts the organization and takes other appropriate actions.
- Software Defined Perimeter (SDP). SDP is a security method that sits on top of the network and hides it from attackers and unauthorized users. Use identity criteria to restrict access to resources and create virtual boundaries around network resources.
- Virtual Private Network (VPN). A VPN secures the connection from your endpoint to your organization’s network. Use tunneling protocols to encrypt information sent over unsecured networks. Remote access VPN allows employees to access your corporate network remotely.
- Web Protection. This practice regulates employee web usage on an organization’s network and devices, including blocking specific threats and websites, as well as protecting the integrity of the organization’s website.
- Wireless Security. Wireless networks are one of the riskiest parts of your network and require rigorous security and monitoring. It’s important to follow wireless security best practices, such as segmenting Wi-Fi users by service set identifier (SSID) and using 802.1X authentication. Securing your wireless network also requires good monitoring and auditing tools.
- Workload security. As organizations balance workloads across multiple devices in cloud and hybrid environments, the potential attack surface increases. Workload security measures and secure load balancers are necessary to protect the data contained in these workloads.
- Zero Trust Network Access. Similar to network access control, zero trust network access gives users only the access they need to do their jobs. Block all other permissions.
Benefits of network security
The main benefits of network security are:
- Working capacity. Network security ensures the continued high performance of the networks that businesses and individual users rely on.
- Privacy and Security. Many organizations work with user data and are required to ensure the confidentiality, integrity, and availability of data across networks, known as the CIA Triad. Network security prevents security breaches that result in disclosure of PII and other sensitive information, damage to company reputation and financial losses.
- Protection of intellectual property. Intellectual property is the key to competitiveness for many companies. Ensuring access to intellectual property related to products, services and business strategies helps organizations maintain a competitive edge.
- Compliance. Compliance with data security and privacy regulations such as HIPAA and GDPR is a legal requirement in many countries. A secure network is an important part of complying with these obligations.
Challenges of network security
Network security comes with many challenges, including:
- Development of network attack techniques. The biggest challenge to network security is the rate at which cyber attacks are increasing. As technology changes, threat actors and their methods constantly change. For example, new technologies like blockchain are giving rise to new types of malware attacks like cryptojacking. Therefore, network security defense strategies must adapt to these new threats.
- User compliance. As mentioned earlier, security is the responsibility of all network users. It can be difficult for organizations to ensure that everyone is following network security best practices while developing strategies to deal with the latest threats.
- Remote and mobile access. More and more companies are adopting a bring your own device policy. This means that the network of devices that organizations must protect becomes more distributed and complex. Remote work is also popular. This makes wireless security even more important as users are more likely to use a personal or public network when accessing a corporate network.
- Third Party Partners. Cloud providers, managed security services, and security product vendors often have access to an organization’s network, exposing new potential vulnerabilities.
The Use of Network Security Protocols
Network security protocols are used to provide critical protection to data flowing over networks. For example, many early network protocols were implemented without data encryption, allowing anyone monitoring network traffic to potentially read sensitive data.
Implementing network security protocols has helped address these potential security risks. For example, Transport Layer Security (TLS) surrounds unencrypted connections with an encrypted wrapper to protect them from potential eavesdropping.
Interesting topic of cybersecurity you did not know
- Ransomware Definition: 6 Types of Variants, Attacks, and How to Prevent?
- 12 types of Phishing attacks: Prevention, causes, techniques and examples
- Cryptography digital signature: Definitions, Algorithms and importance
- Cryptography and network security
- Cryptography: Meaning, Types and best Example—everything is here to know
- What is malware? History, Definition, 7 main types and real-world examples
- 3 Main Objectives of Cybersecurity
- Cybersecurity Goals: 3 major objectives of cybersecurity
The OSI Model
Network protocols are implemented using multiple layers with different purposes. Several frameworks have been developed to model this ecosystem, but the most widely used is the Open Systems Interconnection (OSI) model.
The OSI model divides the network protocol stack into seven layers based on purpose. These seven layers include:
Physical Layer:
Layer 1 is the physical connection between systems, such as electrons traveling over cables.
Data Link Layer:
Layer 2 encodes the traffic bit by bit and sends it to the physical layer with error correction at the physical layer.
Network Layer:
Layer 3 routes packets from source to destination.
Transport Layer:
Layer 4 handles size, ordering, and error correction to ensure that entire packets are delivered to their destination.
Session Layer:
Layer 5 establishes, manages, and terminates the connection between two applications.
Presentation Layer:
Layer 6 converts data between network packets and the format used by higher-level applications.
Application Layer:
Layer 7 implements the services and devices that higher-level applications use to communicate over the network.
Types of Network Security Protocols
Network security protocols are typically designed to provide confidentiality, integrity, authentication, or a combination of the three to network traffic. Below are some examples of widely used network security protocols.
IPsec and Virtual Private Networks (VPNs)
Virtual private networks (VPNs) can operate at different layers of the OSI model. For example, IPsec, a common VPN protocol, runs at Layer 3. However, it is also possible to implement a VPN using HTTPS, which is a Layer 7 protocol.
Regardless of how it is implemented, a VPN is used to create an encrypted tunnel for traffic to pass through. Similar to SSL/TLS, VPNs often begin with a handshake to set the encryption key used to secure network traffic. All subsequent traffic is encrypted by the sender and decrypted by the receiver before being sent over the network.
VPNs can be used in one of two paradigms. Remote access VPNs are designed to connect your computer to a remote server on your corporate network. Site-to-site VPNs, on the other hand, are designed to connect two geographically dispersed networks over the untrusted public Internet.
SSL/TLS
Secure Sockets Layer and Transport Layer Security (SSL/TLS) is a network security protocol that operates at Layer 5 of the OSI model. This protocol provides several benefits to network traffic, including data encryption, authentication, and integrity protection.
An SSL/TLS connection begins with a handshake designed to establish a secure connection between the client and server. During this handshake, the communicating parties agree on the cryptographic algorithms that will be used for encryption, authentication, and integrity checks during the session.
Authentication is also performed during this initial handshake. At a minimum, the server provides an X.509 digital certificate to the client that verifies the identity of the server. However, both systems can also perform mutual authentication during this handshake.
The role of SSL/TLS is to wrap other less secure protocols in an encrypted, authenticated, and integrity-checked wrapper. For example, the HTTPS protocol runs the insecure HTTP protocol inside an SSL/TLS tunnel.
Datagram Transport Layer Security (DTLS)
SSL/TLS is designed to work with Transmission Control Protocol (TCP) to establish a stable and reliable connection. However, User Datagram Protocol (UDP) is another commonly used protocol that provides connectionless transmission.
The Datagram Transport Layer Security (DTLS) protocol operates at Layer 5 of the OSI model and is derived from SSL/TLS, but is designed for use with connectionless and untrusted datagrams. This protocol helps ensure data integrity and confidentiality for applications that require low latency and latency, such as video conferencing, VoIP, and online gaming.
Kerberos
Kerberos is a widely used Layer 7 protocol for authenticating service requests. It is designed to authenticate requests between trusted systems over untrusted public networks.
Kerberos is built on the concept of stamps, which are used to provide proof of identity and authentication. A central authentication server is used to verify the user’s identity and generate these tokens. Every system or application that trusts this server can verify a user’s authority to make a particular request.
Kerberos is supported by most operating systems, including Windows, Mac, and Linux. However, it is the default authentication protocol in Windows and a core component of the Active Directory (AD) service.
SNMPv3
Simple Network Management Protocol (SNMP) is a Layer 7 network protocol for monitoring and managing your organization’s devices. SMTP managers can interrogate the device, and agents on the device respond to these requests or perform the requested action.
Early versions of SMTP were insecure and lacked encryption, authentication, and integrity protection. SNMPv3 is an updated version of the protocol introduced in 2004 that provides all of these features using modern secure cryptographic algorithms.
HTTPS
HTTP is a Layer 7 network protocol used for web browsing. HTTP is one of the earliest network protocols and was implemented as an unencrypted, human-readable protocol.
Anyone monitoring your network traffic can read and modify your HTTP traffic on the way to its destination. The Internet is increasingly being used to transmit sensitive data such as payment card information and login credentials, creating significant security risks.
HTTPS is a secure version of the HTTP protocol that provides data encryption, integrity protection, and authentication. HTTPS was implemented by running HTTP within an SSL/TLS wrapper rather than rewriting the protocol from scratch. Once the SSL/TLS tunnel is established, it provides the necessary encryption, authentication, and integrity protection for the HTTP traffic used to transmit data between the client’s browser and the web server.
Network Security Protection with Quantum
Network security protocols are designed to help protect data flowing over networks. However, some of these protocols require specialized hardware, and none provide protection against common threats such as malware and data leaks.
Network security tools are essential for implementing common network security protocols (such as VPNs) and identifying and blocking malicious traffic accessing an organization’s systems. Check Point has been a leader in network security for many years. More than 30 years of network security innovation has earned Check Point the title of Frost & Sullivan Firewall Company of the Year and recognition as a Leader in the 2022 Gartner® Magic Quadrant™ for Network Firewalls.
follow me : Twitter, Facebook, LinkedIn, Instagram


4 thoughts on “Mastering Network Security: 10 Vital Steps for Ultimate Protection”
Comments are closed.